Comprehensive Guide to Access Control Vulnerabilities
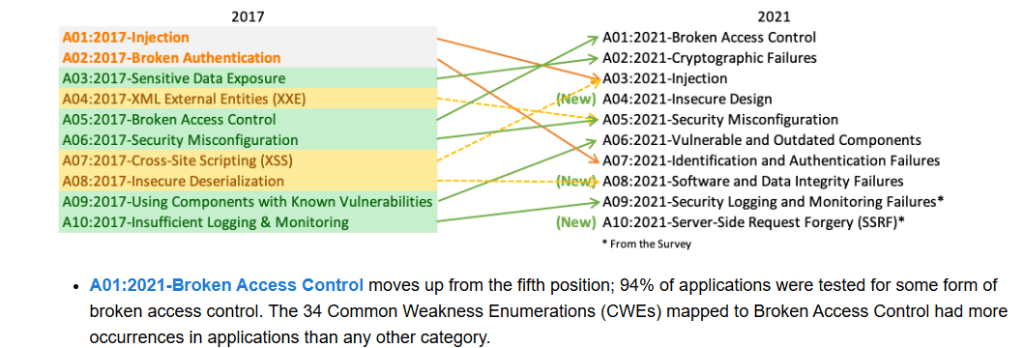
Introduction to Access Control Access control serves as a fundamental security mechanism that governs who can access specific resources on a system and what actions they can perform. At its core, access control ensures that unauthorized individuals are prevented from accessing sensitive data or performing critical operations. It acts as a barrier between legitimate users […]
Penetration Testing Best Practices
One essential security procedure for finding and fixing holes in an organization’s IT infrastructure is penetration testing, often known as pen testing. In order to make sure that thorough security measures are in place, this piece examines the best methods for conducting penetration tests. Introduction to Penetration Testing What is Penetration Testing? Penetration testing is […]