Comprehensive Guide to Access Control Vulnerabilities
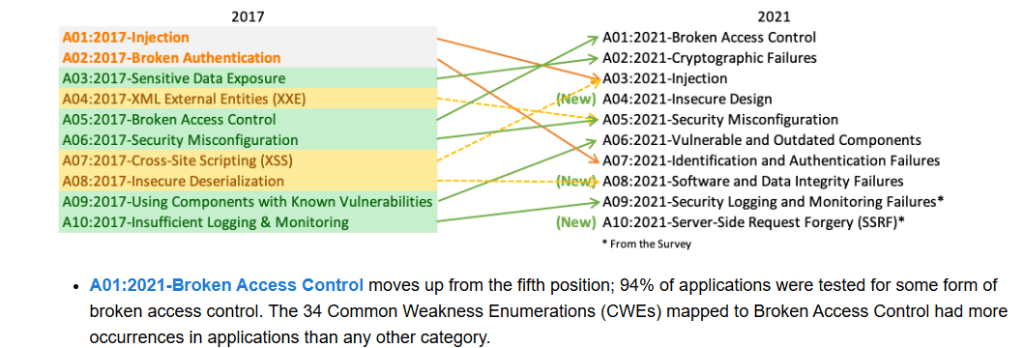
Introduction to Access Control Access control serves as a fundamental security mechanism that governs who can access specific resources on a system and what actions they can perform. At its core, access control ensures that unauthorized individuals are prevented from accessing sensitive data or performing critical operations. It acts as a barrier between legitimate users […]
The Rise of API Security Concerns
APIs are the foundation of modern software development. They enable seamless data sharing between software systems, powering countless applications and services. API security concerns are growing as API use increases. Introduction to API Security Applications’ social media logins and e-commerce transactions depend on APIs. API demand has skyrocketed as businesses embrace digital transformation. This […]
Hunting for Security Misconfigurations
Cybersecurity threats grow in complexity and severity in today’s fast-changing digital world. Security misconfigurations are a major vulnerability for organisations. In this article, we will discuss security misconfigurations’ importance, types, risks, detection methods, prevention methods, real-world examples, and the consequences of ignoring them. Introduction to Security Misconfigurations Security misconfigurations expose systems, applications, and devices to […]
Advanced Techniques in Server-Side Request Forgery (SSRF)
Web applications are vulnerable to Server-Side Request Forgery (SSRF), which allows attackers to manipulate server requests and access sensitive data or perform unauthorised actions. Developers, security professionals, and system administrators must understand advanced SSRF techniques to defend against this attack. Introduction to SSRF What is Server-Side Request Forgery (SSRF)? The Server-Side Request Forgery (SSRF) vulnerability […]
Understanding CSRF (Cross-Site Request Forgery)

In the digital age, cybersecurity threats evolve, including the often misunderstood but devastating Cross-Site Request Forgery (CSRF) attack. CSRF’s history, common attack vectors, impact, prevention, and relevance in modern web applications will be discussed. 1. Introduction to CSRF What is CSRF? Cross-Site Request Forgery (CSRF) targets trusted users to send unauthorised commands to a web […]
The Art of Burp Suite
Cybersecurity professionals and ethical hackers use Burp Suite to test and analyse web applications. It has many features to find vulnerabilities, intercept and modify HTTP traffic, and automate security testing. This article will teach you how to use Burp Suite to improve web application security testing. Introduction to Burp Suite PortSwigger’s Burp Suite is an […]
Demystifying SQL Injection Attacks
SQL injection attacks are one of the biggest threats to web apps and databases worldwide. Attackers can manipulate SQL queries in web applications that use SQL databases using these vulnerabilities. We will explain SQL Injection attacks, their effects, and how to prevent them in this article. Click here to enroll in our premium course and […]
Exploring the World of Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a common web application security vulnerability that lets attackers inject malicious scripts into other users’ web pages. Web developers and users must understand XSS to reduce its risks. Introduction to Cross-Site Scripting (XSS) Web applications that allow users to inject malicious scripts into web pages viewed by other users are vulnerable […]
The Evolution of Bug Bounty Programs
Introduction In the digital age, prioritizing cybersecurity is paramount for businesses and organizations worldwide. Companies are constantly seeking new methods to defend against cyberattacks. In recent years, bug bounty programs have gained considerable popularity. These initiatives utilize ethical hackers to discover and remedy system and software vulnerabilities before malicious actors exploit them. Click here to […]
Cybersecurity Best Practices for Remote Work
Remote work has become more common in the workplace. Global events like the COVID-19 pandemic have accelerated this shift, prompting companies worldwide to adopt remote work policies for business continuity. Remote work offers flexibility and convenience, but organizations must address cybersecurity issues to protect their digital assets and sensitive data. Click here to enroll in […]